Audit & Regulatory Compliance
Managing Ever-Changing Mandates
In today’s hyper-connected digital landscape, organizations face the daunting challenge of ensuring their operations comply with an ever-evolving regulatory standard. With the stakes higher than ever and regulatory bodies becoming more stringent, businesses are constantly on the lookout for efficient and robust solutions to maintain compliance and safeguard their reputation.

The Graylog Approach to Audit & Regulatory Compliance
Graylog solutions are built to mitigate cybersecurity compliance challenges by automating the difficult, compliance knowledge-intensive tasks, automatically archiving all your event log data, and providing out-of-the-box dashboards and report templates that make demonstrating cyber resilience a breeze.
Simplify Compliance Efforts with Graylog Security
Graylog Security is a linchpin in the drive toward achieving and maintaining audit & regulatory compliance. By aggregating and analyzing data from various sources, Graylog Security offers:
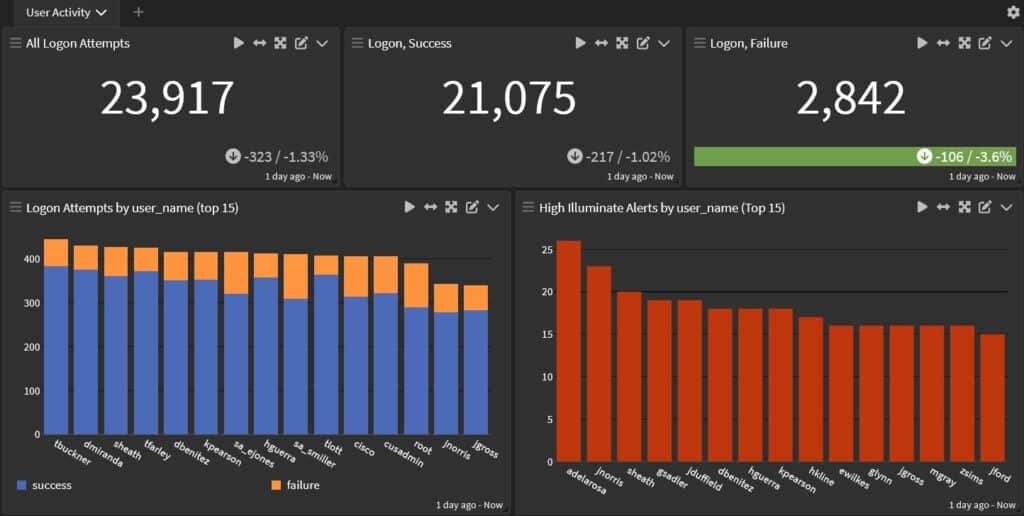
Visibility Across Your IT Environment
Graylog Security provides a bird’s-eye view of your entire organizational infrastructure. Detect anomalies, uphold security protocols, and demonstrate regulatory compliance with comprehensive log monitoring and reporting capabilities.
Rapid Incident Response
With real-time monitoring and intelligent alerting, Graylog Security facilitates rapid detection and mitigation of security threats, ensuring compliance standards are consistently met.
"The most powerful and flexible SIEM and centralized log management system I know."
- T-IN in the Healthcare Industry
Bolster Compliance with Graylog API Security
As your business increasingly relies on APIs to power your operations, the security and compliance of your APIs become paramount. Implementing Graylog API Security can provide:
Robust API Protection
Safeguard your APIs against a multitude of threats with Graylog API Security, ensuring data integrity and service continuity, all while adhering to compliance standards.
Granular Access Control
Define who gets to access what. Graylog API Security can ensure that only authenticated and authorized entities interact with your APIs, maintaining data privacy and regulatory compliance.
Synergy Realized: Graylog Security + Graylog API Security
Combining the strengths of Graylog Security and Graylog API Security can empower you to tackle any compliance challenges head-on. This dual approach can provide:
Holistic Security Posture
Use Graylog Security and Graylog API Security to integrate security measures across your IT environment and APIs seamlessly. With this two-pronged approach, you can achieve a unified defense strategy and simplify compliance management and reporting.

Enhanced Threat Intelligence
Leverage data between system logs in Graylog Security and API interactions in Graylog API Security to help your security teams recognize and respond to sophisticated threats faster, ensuring consistent adherence to regulatory standards.

Ready to Rise Above the Challenge?
The challenge of audit & regulatory compliance is multi-faceted, demanding comprehensive solutions. By leveraging the combined strengths of Graylog Security and Graylog API Security, you can not only meet but exceed compliance requirements. In this tandem approach, you benefit from unparalleled visibility, swift incident response, robust API defenses, and enhanced threat intelligence. Ensure you remain ahead of the curve, safeguarded, and compliant by embracing the synergy of Graylog Security and Graylog AI Security.
Learn More About Audit & Regulatory Compliance
Audit & regulatory compliance is a methodical framework for organizations to systematically review and verify their adherence to legal and ethical standards within particular industry or sector. It involves regular audits to ensure that an organization’s operations, policies, and procedures are aligned with external regulatory bodies and internal policies to manage risk and maintain operational integrity. Graylog Security is designed to help organizations evaluate how well they are adhering to regulatory standards while safeguarding themselves against risks, including financial penalties, legal sanctions, and loss of public trust.
Demonstrating audit & compliance can a) enhance credibility and trustworthiness among stakeholders, including customers, investors, and partners, a valuable asset in building and maintaining business relationships, b) lead to operational improvements by revealing areas for process optimization that can result in increased efficiency, reduced waste, and better resource allocation, and c) foster a culture of accountability and integrity within the organization, essential for attracting and retaining talent, as well as establishing a positive corporate image.
Most industries are subject to some form of regulatory oversight, but the extent and specifics vary greatly. Sectors like finance, healthcare, and energy typically face more stringent regulations due to their critical nature and impact on public safety and welfare. It’s essential for organizations to understand the specific regulatory landscape of their industry, including national laws, state and local regulations, and international regulations if they operate globally.
Regulatory standards are typically reviewed and updated periodically to reflect new legal requirements, technological advancements, and emerging risks. The frequency of updates to compliance standards varies by industry and regulatory body. This could range from annually to every few years, depending on the regulatory authority. It’s crucial for organizations to stay informed about changes in compliance standards. This often involves subscribing to updates from relevant regulatory bodies and seeking guidance from compliance experts to ensure ongoing adherence.
Other Use Cases
Ready to View Plans?
Get the Monthly Tech Blog Roundup
Subscribe to the latest in log management, security, and all things Graylog blog delivered to your inbox once a month.