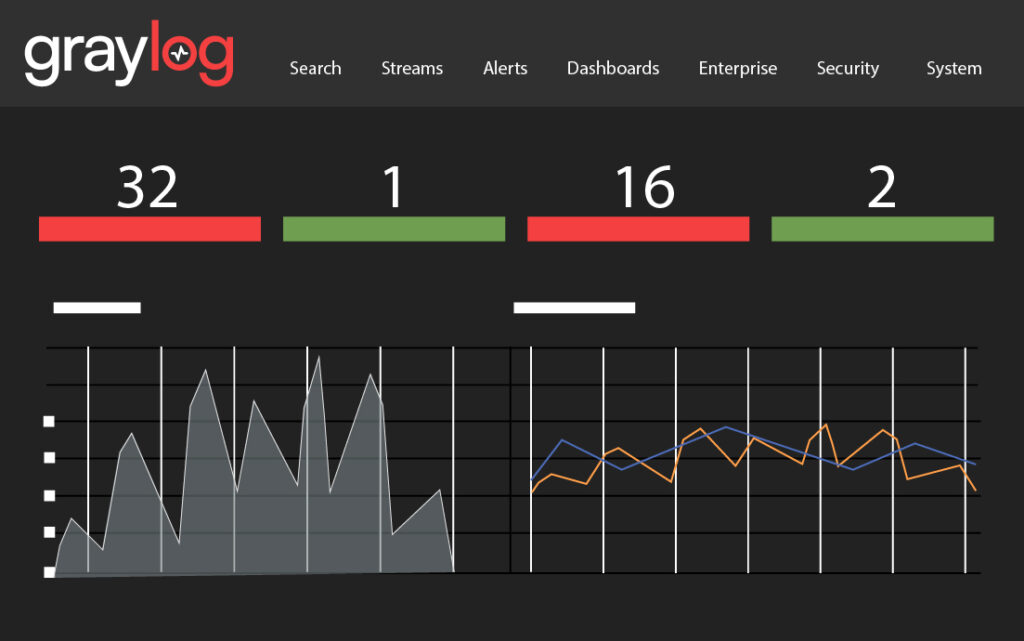
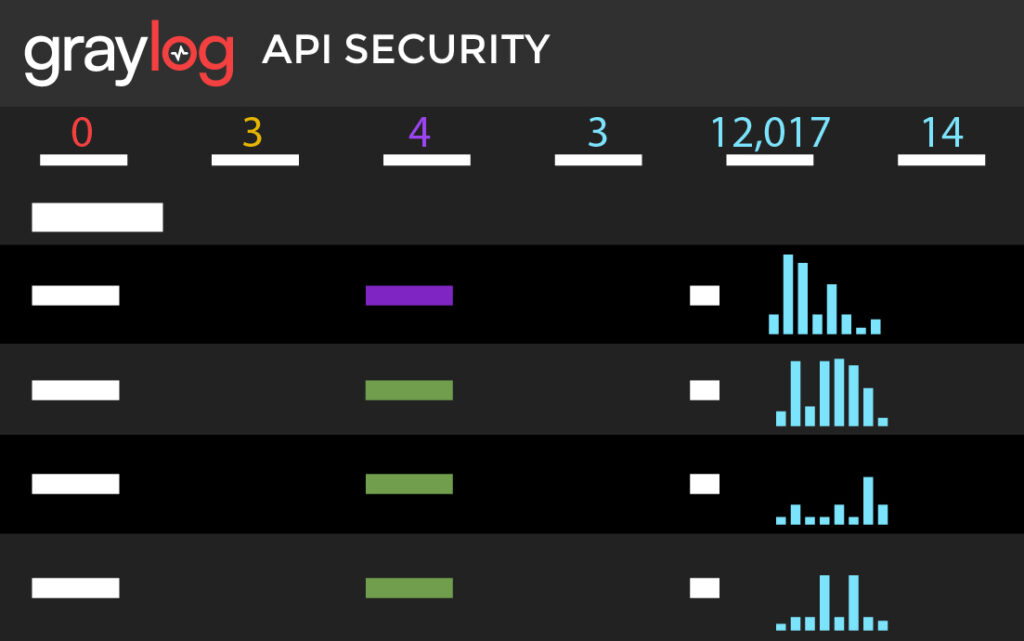
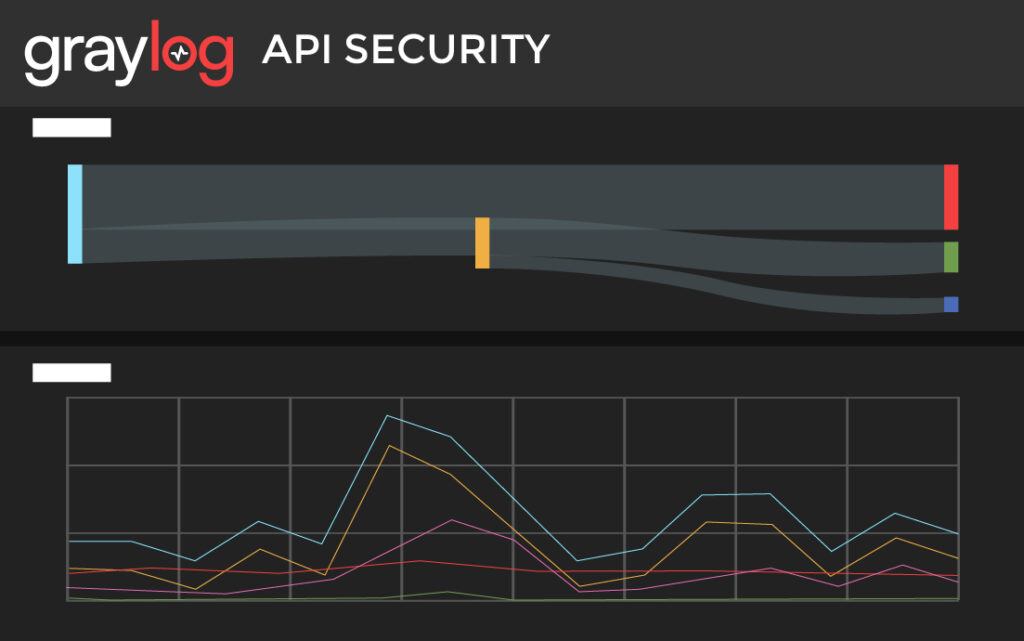
In today’s hyper-connected digital landscape, organizations face a monumental challenge: safeguarding their assets and data against an ever-evolving tapestry of cyber threats. As business operations grow more intricate and intertwined, gaps in security posture can lead to grave consequences, including irreparable security breaches, financial losses, reputational damage, and operational disruptions.