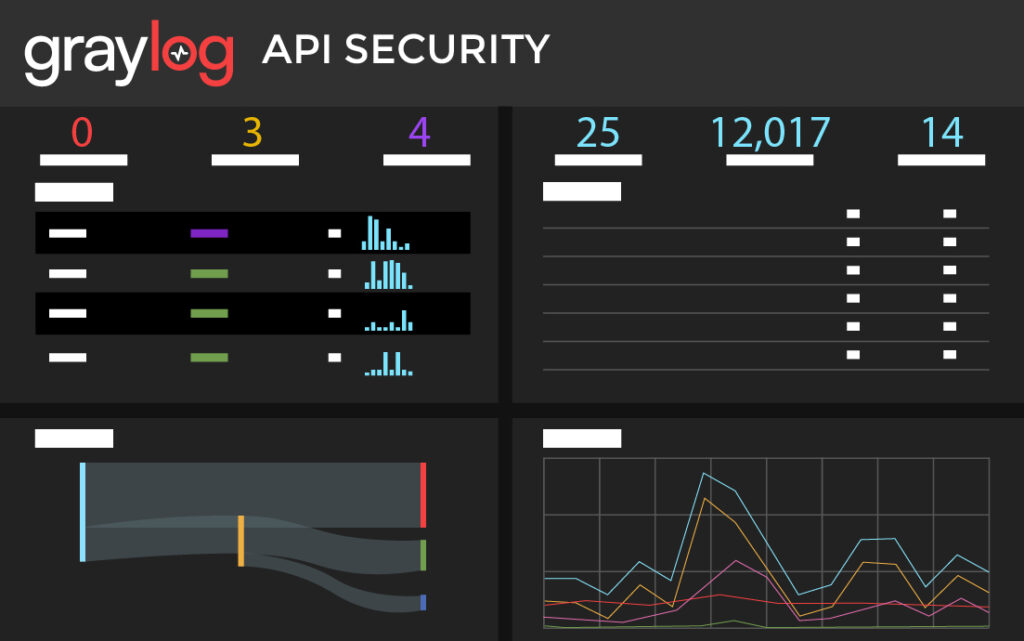
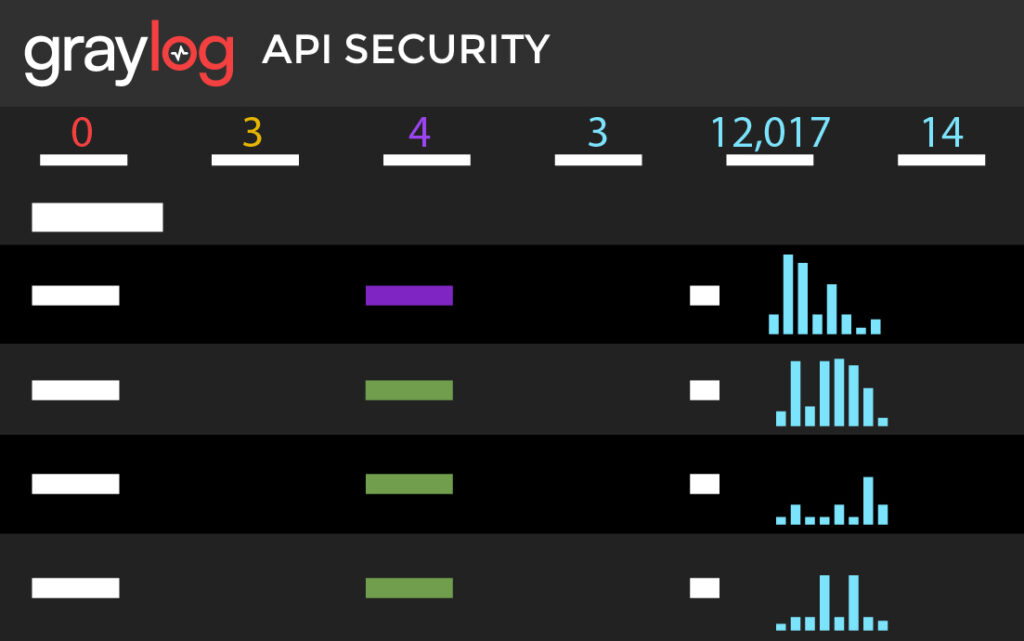
In today’s interconnected world, businesses are more exposed than ever to a vast array of cyber threats. From malware to ransomware, phishing to DDoS attacks, organizations constantly grapple with the challenge of identifying and responding to threats in real time. Failure to do so can result in data breaches, financial losses, damaged reputation, and regulatory fines.